Google has exclusive access to a browser API
And why this is wrong for many reasons
Last week Luca Casonato reported on his Twitter profile an interesting case about browser APIs.
In 2023, Google released a hidden browser extension in Chrome that uses a set of browser APIs exposing the usage of the CPUs, and this is nothing impressive: just another browser API that can be used from web applications.
Or better: just another Browser API that any Google web application can use.
Yes, you read it correctly: the API is available only if you’re loading a page inside the Google domains.
Want to try?
Open the console of your browser on any non-Google page and paste this code (thanks Simon Willison )
chrome.runtime.sendMessage(
"nkeimhogjdpnpccoofpliimaahmaaome",
{ method: "cpu.getInfo" },
(response) => {
console.log(JSON.stringify(response, null, 2));
},
); Here is my result with the Google.com page open:
and on another website.
As a Google spokesperson stated, the API is used
To improve the user experience by optimizing configurations for video and audio performance based on system capabilities.
To provide crash and performance issue reporting data to help Google services detect, debug, and mitigate user issues.
So, everything is fine, right?
Well, yes and no.
While I don’t believe Google has any interest in using these metrics for fingerprinting users or other malicious activities, it doesn’t seem to be a fair move.
These metrics are available for any other extension developer, but if you want to access them directly from the browser without installing any third-party software, you cannot do it, only Google websites can read them.
Zoom, Teams, or any other videoconferencing tool running on a browser, don’t they have the same rights as Meets to know if the CPU keeps the pace of the video call?
Browsers are our entry point to the web, and they should not choose who’s in and out of anything on our behalf.
Microsoft has been forced to let Windows users decide which browser they wanted on their machine.
Chrome itself gives you the opportunity to switch from Google to other search engines (while paying Billions to phone manufacturers to keep this option buried)
But these cases were evident to everyone, so they could not be ignored by regulators.
I have my doubts that anything will happen to Google even if they decide to add the same “walled garden policy” to many other Browser APIs. It’s a subject too technical to be completely understood by the regulators, who won’t act until this practice damages the consumers and the competition in a much greater way than is doing actually.
We can’t opt out of the browsers’ API
Actually there are more than 8k APIs in Chrome, and probably a similar number in other browsers, in order to keep the website’s rendering similar between them.
This means we have 8k+ single data points describing our hardware, software, browsing history, devices connected, and much more. This is why anti-bot solutions have found fertile ground in gathering data from our browsers to build softwares more and more effectively over time.
While this is good for fraud detection and other criminal activities, these signals can be used for other purposes: marketing (even more so after the decreasing importance of cookies) but also surveillance via fingerprinting.
I’ve already written about the latest papers about browser fingerprinting in this post, where we can see how granular and invasive could be this technique.
The biggest issue with fingerprinting is that, while cookies can be canceled, the only way to prevent websites from collecting fingerprinting is to disable JavaScript at a browser level. Unluckily most of the time this solution breaks the usability of the websites, making it impossible for the user to browse them.
The idea of having standard Browser APIs for the web is great: enables web developers to adapt websites between different hardware and software configurations.
But when these pieces of information are used by companies to get advantages in the case of Google, this undermines the idea of the original idea of the open web.


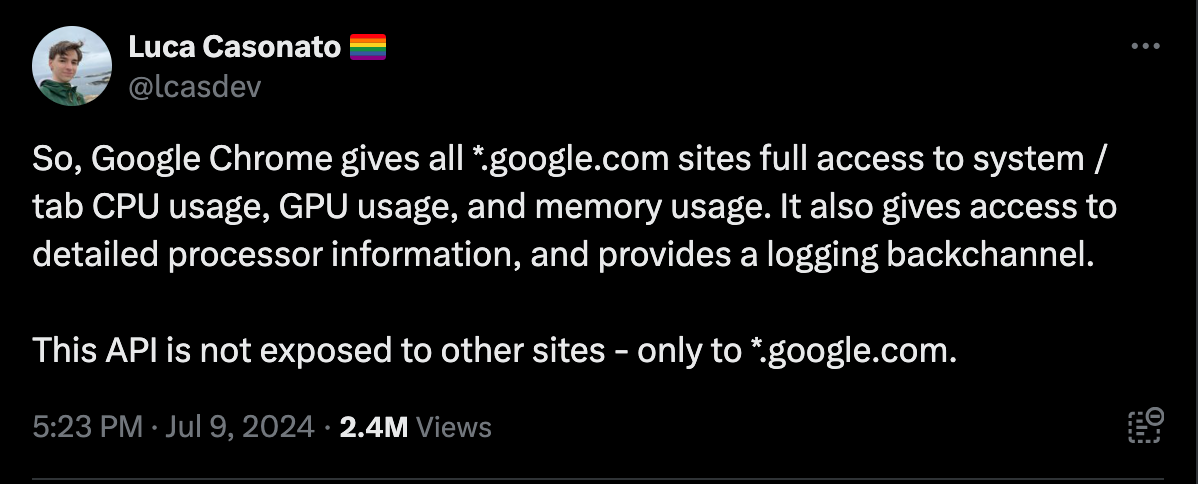




This is majorly concerning. My trust in Google is extremely low, these types of findings validate my concerns.