The Anti-Detect Browser Royal Rumble
Using anti-detect browsers with CreepJS and Browserscan tests
Anti-detect browsers are softwares designed to create legit fingerprints in order to allow their users to simulate a variety of different profiles, with different hardware and software. As the device and browser fingerprinting is getting more spread across anti-bot solutions, these softwares are gaining momentum also in the web scraping industry, being a valid commercial alternative to homemade / OSS solutions like Undetected Chromedriver or undetected-playwright.
In this series of articles called "The Anti-detect Browsers Benchmark", we’re testing these solutions for a better understanding of their features and what we should be aware of when using them for web scraping.
A special thanks go to all the companies involved in this project since they provided me with a free demo for doing all the tests needed: this article could not have been written without them.
In this edition, we’ll compare the performances of the following anti-detect browsers:
Testing methodology
In this edition, we’re going to test the performances of these anti-detect browsers against two famous fingerprinting test pages: Creepjs and BrowserScan.
For every browser we’ll follow these steps:
The download of their client on a Windows Server virtual machine hosted on an AWS data center.
Create a profile that needs to mimic a Mac OS Desktop using a Chrome browser
Add residential proxies located in the same region of the datacenter (eu-central-1)
Disable WebRTC features to avoid the original IP leak
Add noise on Canvas and WebGL renderer and in any other parameter possible.
After setting up the profiles, we’ll visit the two test pages and assign a score from 0 to 260, split as follows:
From 0 to 100 points according to the trust score of the CreepJS test.
From 0 to 100 points according to BrowserScan fingerprint authenticity
20 points if the browser is correctly recognized on both websites, 10 if only in one.
20 points if the operating system is correctly recognized on both websites, 10 if only on one
20 points if there’s no sign of a WebRTC leak on both
All these tests are created by myself without any help from the companies, that are not aware of the final score until the publishing of this article.
The purpose of this article is to use the same methodology for every user and not maximize the score for every test, a thing that could be probably achieved by playing around with some other options.
Anyway, I’m open to reviewing the test results if needed, so please write me at pier@thewebscraping.club if you think there are errors in the evaluations.
Setting the baseline
Given the formula to calculate the score, let’s see what happens by browsing the two test pages directly from my Mac with Chrome.
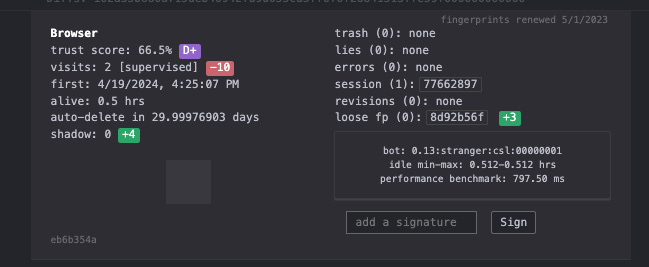
On CreepJS, I’ve got a 66% trust score, while on Browserscan my score is 100%
Of course, the browser and the operating system are correctly recognized on both websites, while there’s no sign of WebRTC leak since I’m not using any proxy.
As a result, we have a baseline score of 226 out of 260 points.
Let’s see how the other browsers behave using the same criteria.
GoLogin
The GoLogin browser on BrowserScan has a perfect 100% fingerprint authenticity
while on CreepJS the trust score is slightly below the baseline, but confirms a good score.
As far as I could interpret the negative signal on the test
probably the GPU spoofing doesn’t seem too coherent with the rest of the fingerprint.
Browser and OS are correctly shown on both the websites
so the final score is 223, a good score if compared with the baseline of 226.
Incogniton
This test has been trickier than the others.
As specified in the testing methodology, every profile we create has added some noise in the Canvas and WebGL fingerprint, to mask the fact that we are running these browsers on a Windows Server.
By doing so with Incogniton, we get a low trust score on CreepJS and less than 100% trust on Browserscan.
The issues on both websites seem to be the inconsistent fingerprint generated since the two websites detect in it some “lies”.
Navigating through the Incogniton’s profile options, I’ve noticed one called “Try to pass Iphey.com check” which effectively gives a boost on both the trust scores, but disables the canvas fingerprint, exposing that we’re on a Windows Machine.
Summarizing the score: we have 14 from CreepJS, 85 from Browserscan, and 20 from the correct detection of Chrome but on the OS since both sites raise warnings on the possible spoofing of information. This makes 119 + 20 for the correct disabling of WebRTC, which gives a total score of 139.
Kameleo
According to CreepJS, the score is 45%, so quite good, with the only red flag raised about the noise in the audio fingerprint.
Another issue is with the operating system, that CreepJS detects as Windows instead of Chrome.
On Browserscan, instead, while everything is correct it seems that the real IP address is leaked.
So the total score is 45 from CreepJS + 90 from Browserscan, plus 20 for the browser correctly detected, 10 for the operating system correct only on Browserscan and the IP correct on CreepJS, for a total score of 175.
MoreLogin
A similar situation happened with MoreLogin. We’ve got a slightly better trust score, lowered by the system fonts that are not coherent with the OS.
In fact, given all the information available, CreepJS thinks that the OS is Windows.
On BrowserScan instead, the only issue is related to the DNS leak, which means that the browser still resolves the domain name through the local operator’s DNS while using a proxy.
Summing up all the information, we have a score of 198.
NSTBrowser
NSTBrowser has a score very close to the baseline, with a score of 63.5% and the correct detection of both OS and Browser.
BrowserScan detects the noise added in the Canvas fingerprint, but OS, Browser, and WebRTC are ok, with an overall score of 95%.
The total score for NSTBrowser is 218.
Octo Browser
Octo Browser seems to add noise to the fingerprint in a way that doesn’t match the expectations of the CreepJS test.
In fact, the score is particularly low, and also the OS is not detected correctly.
On the other hand, it has a 100% score on Browserscan, reaching a total score of 164 for this test.
Undetectable.io
Similar behavior can be seen when testing Undetectable.io, with a score of 59 on CreepJS and the OS not detected, while we have a 100% score on Browserscan.
The total score for Undetectable.io is 209 and it’s due to the noise added in the Canvas fingerprint that lower the score on CreepJS.
Final considerations and ranking
Let’s recap all the scores we’ve seen for the browsers with a final ranking.
After the baseline, the first browser we find is GoLogin with a score very close to the baseline, and then soon after a few points NstBrowser and Undetectable.io.
We need to consider that tests like the Creepjs one are OSS projects created to educate about browser fingerprinting, and a low score in these tests doesn’t necessarily mean that you cannot use the browser for web scraping. In fact, it’s extremely easy to get a low score even using a standard browser and anti-bot softwares cannot afford to ban real users with a low score based on this testing methodology. On the other hand, these tests are great for understanding how coherent is a fingerprint generated by an anti-detect browser, which is always a good starting point for a web scraping project.
In the next episode of the benchmark, we’ll put these anti-detect browsers under stress by using them in real-world web scraping projects and see how they behave against anti-bots.



















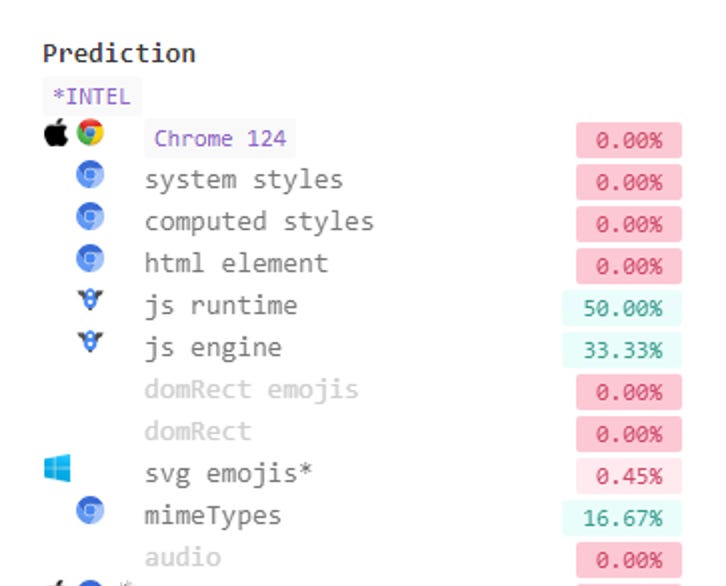





Hey, Pier! There's an issue with this test that impacts the validity of the results. Some browsers, like Gologin, don't actually add any audio noise in the fingerprint, even if you turn it on in settings. As a result, they appear superior compared to other solutions. You can confirm this by creating two Gologin profiles and comparing their audio hashes - they will be identical. Conversely, with Octo, you'll find different hashes, showcasing its proper functionality.
It would be more accurate to test all participants without the addition of audio noises. Could you include this information in the article? We're more than willing to provide further expertise to educate the community and prevent the spread of misinformation.
Is someone running these browsers at scale inside docker containers? If yes can you please share your learnings.
eg: I see there is a docker container for gologin https://github.com/gologinapp/docker but this didn't work out of the box. Also doesn't seem to have been updated in a while.